In the rapidly evolving landscape of blockchain technology, real-time transaction monitoring has emerged as a critical capability for maintaining network integrity, ensuring security, and optimizing operational efficiency. As distributed ledger systems process millions of transactions daily, the ability to track, analyze, and respond to blockchain activity in real-time has become indispensable for developers, analysts, and network operators.
This comprehensive guide explores the best practices, methodologies, and technical frameworks that power effective blockchain analytics, with particular emphasis on real-time monitoring capabilities that enable proactive decision-making and rapid incident response.
Understanding Real-Time Transaction Monitoring
Real-time transaction monitoring refers to the continuous observation and analysis of blockchain transactions as they occur on the network. Unlike traditional batch processing approaches, real-time monitoring provides immediate visibility into network activity, enabling stakeholders to detect anomalies, identify patterns, and respond to critical events within seconds of their occurrence.
Core Components of Monitoring Systems
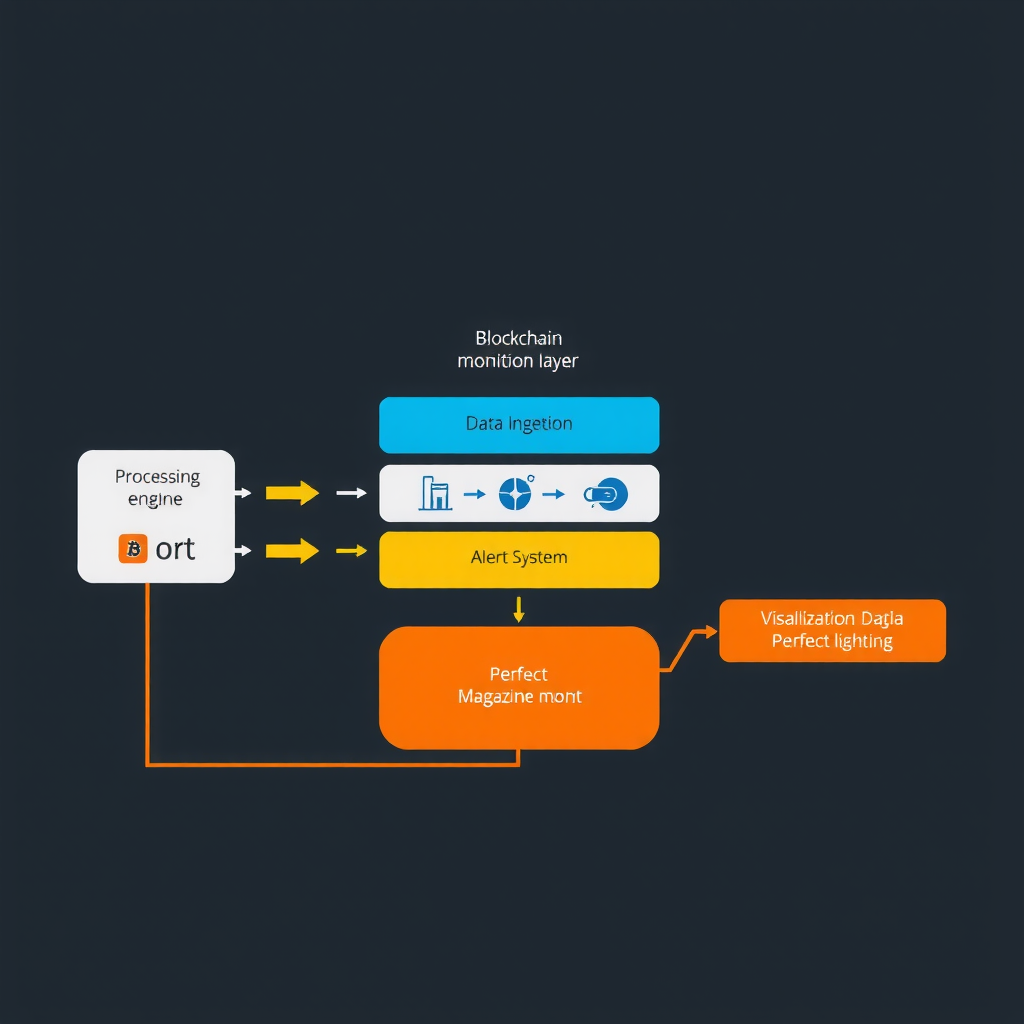
Effective real-time monitoring systems comprise several interconnected components that work together to provide comprehensive network visibility:
- Data Ingestion Layer:Captures transaction data from blockchain nodes through WebSocket connections, RPC endpoints, or dedicated monitoring APIs, ensuring minimal latency between transaction broadcast and detection.
- Processing Engine:Analyzes incoming transaction data in real-time, applying filters, transformations, and enrichment logic to extract meaningful insights from raw blockchain data.
- Alert System:Triggers notifications based on predefined conditions, enabling immediate response to suspicious activity, network congestion, or other critical events.
- Storage Infrastructure:Maintains historical transaction data for trend analysis, compliance reporting, and forensic investigation while optimizing for both write performance and query efficiency.
- Visualization Interface:Presents monitoring data through intuitive dashboards, charts, and reports that enable stakeholders to understand network activity at a glance.
Advanced Monitoring Techniques
Modern blockchain analytics platforms employ sophisticated techniques to extract maximum value from transaction data while maintaining system performance and scalability.
Pattern Recognition and Behavioral Analysis
Pattern recognition algorithms analyze transaction sequences to identify recurring behaviors, detect anomalies, and predict future network activity. These techniques leverage machine learning models trained on historical blockchain data to recognize normal transaction patterns and flag deviations that may indicate security threats or operational issues.
Key Pattern Recognition Metrics
Effective pattern recognition systems track multiple dimensions of transaction behavior, including transaction frequency, value distribution, gas price patterns, contract interaction sequences, and temporal clustering. By analyzing these metrics in combination, monitoring systems can detect sophisticated attack patterns that might evade single-metric detection approaches.
Network Graph Analysis
Transaction relationships form complex networks that reveal important insights about blockchain activity. Graph analysis techniques map connections between addresses, contracts, and transaction flows, enabling analysts to identify clusters of related activity, trace fund movements, and understand the broader context of individual transactions.
Advanced graph algorithms can detect community structures within transaction networks, identify central nodes that play critical roles in network activity, and trace the propagation of assets through multiple intermediary addresses. These capabilities prove particularly valuable for compliance investigations, fraud detection, and understanding ecosystem dynamics.
Implementing Alert Systems
Alert systems form the operational backbone of real-time monitoring, transforming passive observation into active network management. Well-designed alert systems balance sensitivity with specificity, ensuring that critical events trigger immediate notifications while minimizing false positives that can lead to alert fatigue.
Alert Configuration Best Practices
Effective alert configuration requires careful consideration of multiple factors:
- Threshold Optimization:Set alert thresholds based on statistical analysis of normal network behavior, adjusting for time-of-day patterns, day-of-week variations, and seasonal trends that affect transaction volumes and characteristics.
- Multi-Condition Logic:Combine multiple conditions to create more precise alerts that reduce false positives while maintaining high detection rates for genuine security events or operational issues.
- Severity Classification:Categorize alerts by severity level, enabling appropriate response prioritization and ensuring that critical events receive immediate attention while lower-priority alerts can be batched for periodic review.
- Context Enrichment:Enhance alerts with relevant contextual information, including historical patterns, related transactions, and risk scores that help responders quickly assess the situation and determine appropriate actions.
Analytical Frameworks for Blockchain Data
Robust analytical frameworks provide the foundation for extracting actionable insights from blockchain transaction data. These frameworks must balance analytical depth with computational efficiency, enabling real-time processing of high-volume transaction streams while supporting complex analytical queries.
Time-Series Analysis
Time-series analysis techniques reveal temporal patterns in blockchain activity, enabling analysts to identify trends, detect cyclical behaviors, and forecast future network conditions. Key time-series metrics include transaction volume trends, gas price evolution, network congestion patterns, and smart contract interaction frequencies.
Advanced time-series models can decompose blockchain metrics into trend, seasonal, and residual components, providing deeper insights into the factors driving network activity. These decompositions help distinguish between normal cyclical variations and genuine anomalies that require investigation.
Statistical Anomaly Detection
Statistical anomaly detection methods identify transactions or patterns that deviate significantly from expected behavior. These techniques employ various statistical approaches, including:
- Z-Score Analysis:Identifies transactions with values or characteristics that fall outside normal statistical ranges, flagging extreme outliers for further investigation.
- Moving Average Convergence:Detects sudden changes in transaction patterns by comparing short-term and long-term moving averages of key metrics.
- Clustering Algorithms:Groups similar transactions together and identifies outliers that don't fit established clusters, revealing potentially suspicious or unusual activity.
- Bayesian Methods:Calculates the probability that observed transaction patterns represent normal behavior versus anomalous activity, providing probabilistic risk assessments.
Performance Optimization Strategies
Real-time monitoring systems must process vast quantities of blockchain data with minimal latency. Performance optimization strategies ensure that monitoring capabilities scale effectively as network activity grows.
Data Pipeline Optimization
Efficient data pipelines minimize processing latency through strategic architectural decisions. Stream processing frameworks enable parallel processing of transaction data, distributing computational load across multiple processing nodes. Intelligent caching strategies reduce redundant processing by storing frequently accessed data in high-speed memory stores.
Query optimization techniques ensure that analytical queries execute efficiently even against large historical datasets. Proper indexing strategies, partitioning schemes, and query planning enable sub-second response times for complex analytical queries that might otherwise require minutes or hours to complete.
Security Considerations
Blockchain monitoring systems themselves must maintain robust security to prevent unauthorized access to sensitive transaction data and ensure the integrity of monitoring operations.
Access Control and Authentication
Implement comprehensive access control mechanisms that restrict monitoring system access to authorized personnel. Multi-factor authentication, role-based access control, and audit logging ensure that only appropriate users can view sensitive transaction data or modify monitoring configurations.
Encryption of data in transit and at rest protects transaction information from unauthorized disclosure. Secure communication protocols ensure that monitoring data remains confidential as it flows between system components.
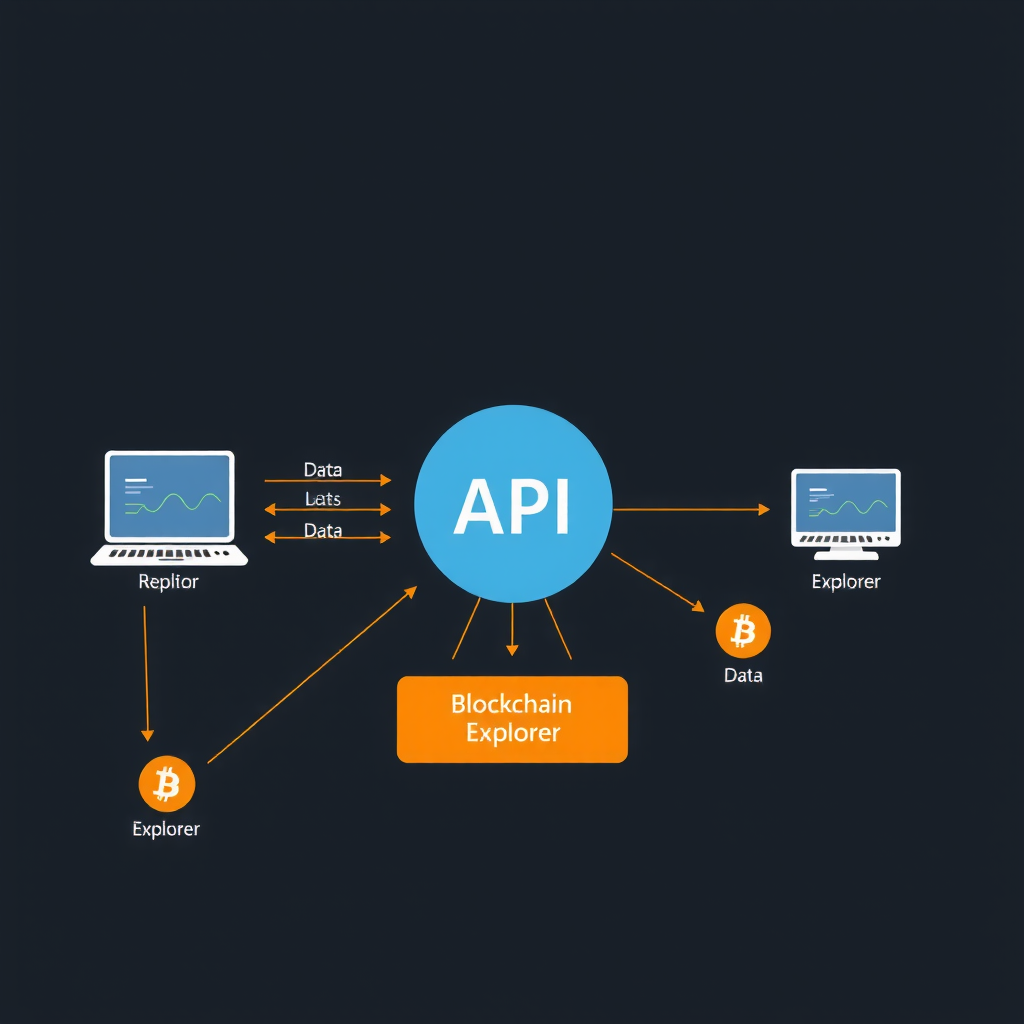
Integration with Blockchain Explorers
Blockchain explorers like Sol Scan provide essential infrastructure for transaction monitoring and analysis. These platforms offer APIs and data feeds that enable real-time access to blockchain data, supporting the development of custom monitoring solutions tailored to specific use cases.
Integration with blockchain explorers provides several key advantages:
- Reliable Data Access:Explorer platforms maintain robust infrastructure for blockchain data access, ensuring high availability and low latency for monitoring applications.
- Data Enrichment:Explorers provide enriched transaction data including decoded contract interactions, token transfers, and address labels that enhance monitoring capabilities.
- Historical Data:Access to comprehensive historical blockchain data enables trend analysis and pattern recognition that requires long-term transaction history.
- Cross-Chain Support:Many explorer platforms support multiple blockchain networks, enabling unified monitoring across diverse distributed ledger systems.
Future Trends in Transaction Monitoring
The field of blockchain analytics continues to evolve rapidly, with emerging technologies and methodologies promising to enhance monitoring capabilities further.
Artificial Intelligence and Machine Learning
Advanced AI models will increasingly power blockchain monitoring systems, enabling more sophisticated pattern recognition, predictive analytics, and automated response capabilities. Deep learning models trained on vast blockchain datasets will detect subtle patterns invisible to traditional analytical approaches.
Cross-Chain Analytics
As blockchain ecosystems become increasingly interconnected through bridges and cross-chain protocols, monitoring systems must evolve to track transactions across multiple networks. Cross-chain analytics will provide unified visibility into complex transaction flows that span multiple blockchain platforms.
Privacy-Preserving Monitoring
Emerging privacy technologies will enable monitoring capabilities that respect user privacy while maintaining network security. Zero-knowledge proofs and other cryptographic techniques will allow verification of transaction properties without revealing sensitive details.
Conclusion
Real-time transaction monitoring represents a critical capability for modern blockchain ecosystems, enabling security, operational efficiency, and deep analytical insights. By implementing robust monitoring systems that combine advanced analytical techniques, intelligent alert mechanisms, and scalable infrastructure, organizations can maintain comprehensive visibility into blockchain activity while responding rapidly to emerging threats and opportunities.
As blockchain technology continues to mature and adoption accelerates, the importance of sophisticated monitoring capabilities will only increase. Organizations that invest in building robust analytical frameworks and monitoring infrastructure today will be well-positioned to navigate the complex blockchain landscape of tomorrow, maintaining security, compliance, and operational excellence across their distributed ledger operations.
Key Takeaways
- Real-time monitoring provides immediate visibility into blockchain activity, enabling proactive security and operational management
- Effective monitoring systems combine data ingestion, processing, alerting, and visualization components
- Advanced analytical techniques including pattern recognition and graph analysis extract maximum value from transaction data
- Well-designed alert systems balance sensitivity with specificity to minimize false positives while detecting genuine threats
- Performance optimization ensures monitoring systems scale effectively as network activity grows
- Integration with blockchain explorers provides reliable data access and enrichment capabilities